Your AI agents have gone into production, is your security monitoring catching up?
Ackuity gives you Realtime Threat Detection and Response for Agentic AI
.png)
Ackuity covers your entire Agentic Infrastructure for security monitoring
Detect threats on AI agents and Gen AI Applications
Detects threats when users interact with AI agents and applications
Detect threats when AI agents interact with enterprise systems
Discover AI agents
AI agents, both commercial and custom are deployed in various departments in your organization. With Ackuity you get visibility of all the AI agents in your environment and their connections
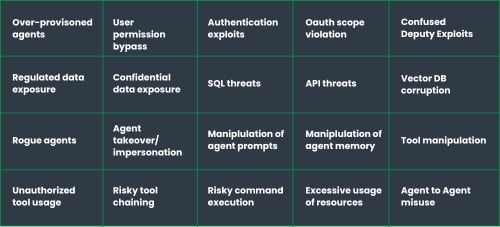
Detect threats to AI
Ackuity goes beyond guard rails by monitoring for threats in interactions between users and agents, and between agents and back end systems. Ackuity is configured with over hundred rules and models to detect across all the NIST and OWASP Agentic AI threat categories.
Enforce
With Ackuity you can block or mask sensitive data in responses to comply with policies. Ackuity stops malicious activity, including API attacks, SQL injection, and abnormal agent behavior.
Get Visibility
Get visibility across all agents and all interactions between users, agents and backend systems. Centralized logging, auditing and monitoring of agent interactions including connections, access, queries, and responses. Ensure compliance and simplify audits.
.png?width=90&height=90&name=Untitled%20(3).png)
“Ackuity helps in discovery and real time threat detection & response for Agentic AI. Our pilot demonstrated the same for an AI Agent interacting with SharePoint, Entra and MS purview, securing against threats of information leakage, permission bypass and policy violations.”
Akundi Sarma, Architect, CA&I, Unisys
Ackuity in Action: Threat Detection and Response for Agentic AI

Key Components of Ackuity
Ackuity has following built-in components to secure Agents and RAG pipelines
Ackuity secures every layer in your agentic AI

Where Ackuity Fits in the GenAI Security Puzzle
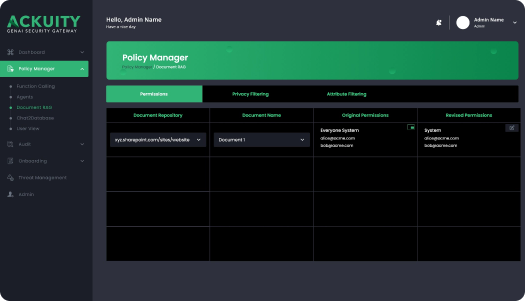
Ackuity is not a prompt filtering or prompt security or prompt guardrail solution.
There are multiple GenAI solutions in market and these are still evolving. Learn what are these solutions, where do they fit in your GenAI projects and how Ackuity is different from them.
Ackuity Blog






Get further information by Contacting with Our Experienced IT Professionals.
We’re available for 8 hours a day!
Contact to require a detailed analysis and assessment of your plan.
