
Monitoring and Logging
GenAI applications interact with many document stores, data stores, enterprise applications, identity systems, digital devices, and more. These interactions must be logged for security, observability, and transparency, and to allow easy RCA for critical issues.
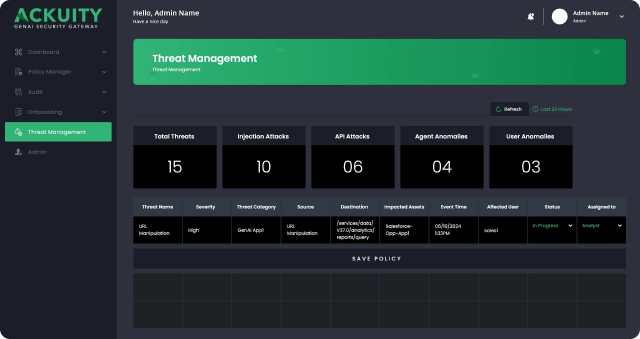
Ackuity can create extensive logs of GenAI application interactions
Query logging
Ackuity logs all queries a GenAI application sends and receives to different systems. This includes semantic queries, vector DB queries, SQL queries to data warehouses, and API queries to enterprise applications. Ackuity automatically correlates queries to users, and captures all attributes of the query including timestamp, user, and source and destination IP and destination system information.

Agent action logging
Ackuity offers a secure gateway that GenAI agents pass through to execute autonomous actions on enterprise applications (like scheduling meetings in Outlook, or scheduling a report in Salesforce). Ackuity logs all agent actions, including key attributes like user information, source and destination IP information, source and destination system information, timestamps for each phase of actions, and API calls used.

Authentication and authorization logging
Ackuity logs all interactions and captures key information related to authentication and authorization with GenAI applications. This includes users authenticating with GenAI applications, GenAI seeking authorization for users, GenAI authenticating with LLMs, GenAI authenticating and authorizing vector DB and semantic search, and the like.
